Security And Monitoring
At Pathfix, security is crucial and of the utmost importance. We do not store any user level data, data is fetched in real-time and sent directly to your database.
SECURITY OVERVIEW
Secure At The Core
We go above and beyond to protect our customer data and are committed to providing a secure solutions.
SECURITY MEASURES WITH PATHFIX
Application Level Firewall
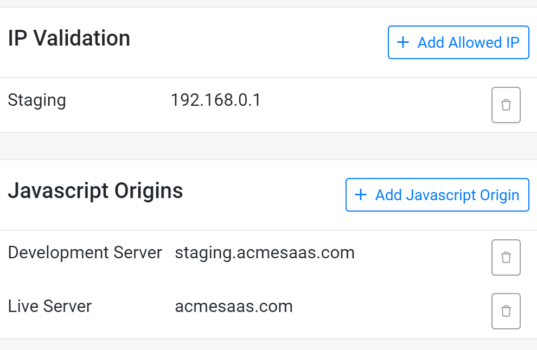
Pathfix allows for application level firewall settings. The settings allow requests generated from specific IP address or requests from specified domains as JavaScript Origin to be granted.
IP Firewall
Configurable firewall settings across platform so that any connection attempts from the internet must pass through the firewall before they are passed onto the service provider.
When a computer tries to make server-side API requests from the internet, the firewall first checks the originating IP address of the request against the set IP firewall rules.
JavaScript Origins Firewall
Configurable security setting that allow you to set authorized JavaScript origins of the applications/domains that use JavaScript to make authorized OAuth requests. The origins identify the domains from which your users send requests.
When an origin tries to make requests, the firewall will first check the origin of the request against the set JavaScript origins.
Data Encryption At-Rest And In-Transit
All Access Tokens and Refresh Tokens associated with user accounts are encrypted and stored on cluster servers designed to prevent brute-force attacks even in case of a breach.
Data-at-rest and in-motion is encrypted with advanced encryption standard, making it not only unreadable to human eyes but also inaccessible from any attack.
Security Management
Pathfix servers and encryption algorithms go through stringent penetration and vulnerability audits ensuring that our servers and data are always secured.
Monitoring Logs
Additional layer of security is added by means of data purge. All activity monitoring logs, transactional data, are automatically purged from the system in 30 days.

